
A IT Security Audit Checklist is a comprehensive tool used to evaluate the effectiveness of an organization's information security measures. It helps identify vulnerabilities, ensure compliance with security policies, and verify that controls are properly implemented. Regular use of this checklist enhances data protection and reduces the risk of cyber threats.
IT security audit checklist for small businesses
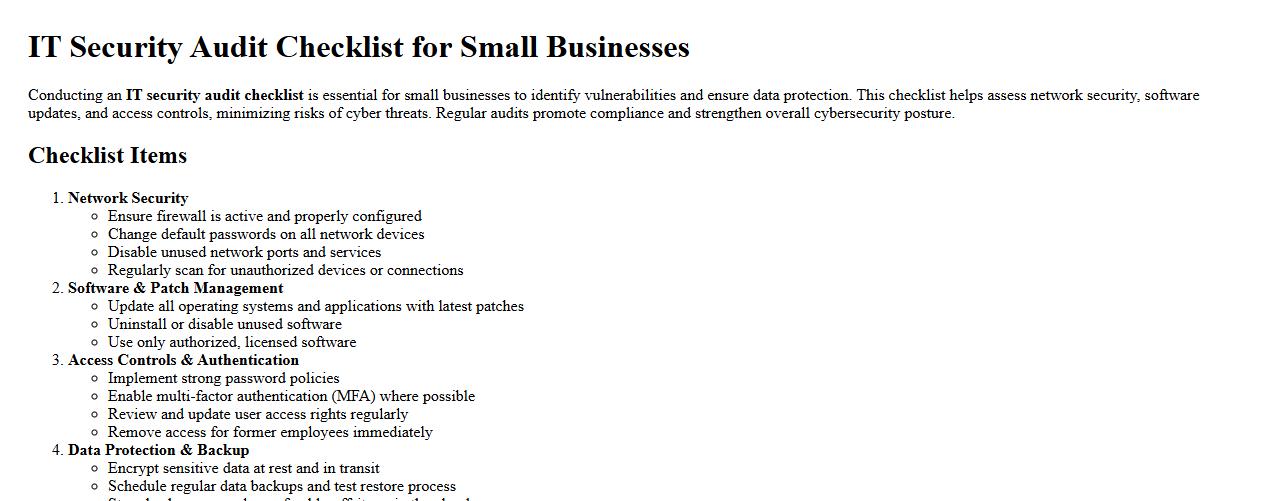
Conducting an IT security audit checklist is essential for small businesses to identify vulnerabilities and ensure data protection. This checklist helps assess network security, software updates, and access controls, minimizing risks of cyber threats. Regular audits promote compliance and strengthen overall cybersecurity posture.
IT security audit checklist for financial institutions
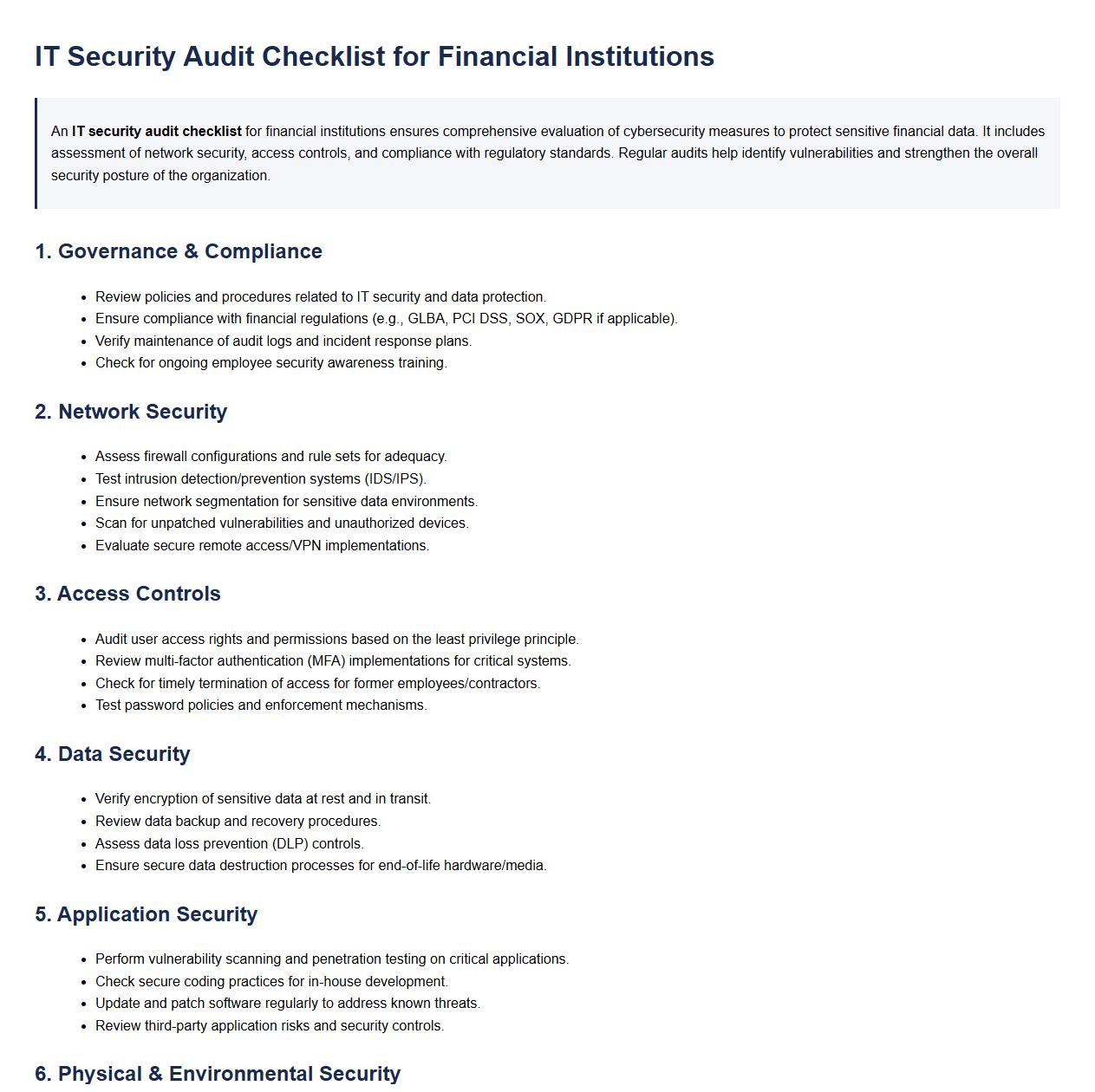
An IT security audit checklist for financial institutions ensures comprehensive evaluation of cybersecurity measures to protect sensitive financial data. It includes assessment of network security, access controls, and compliance with regulatory standards. Regular audits help identify vulnerabilities and strengthen the overall security posture of the organization.
IT security audit checklist for healthcare organizations
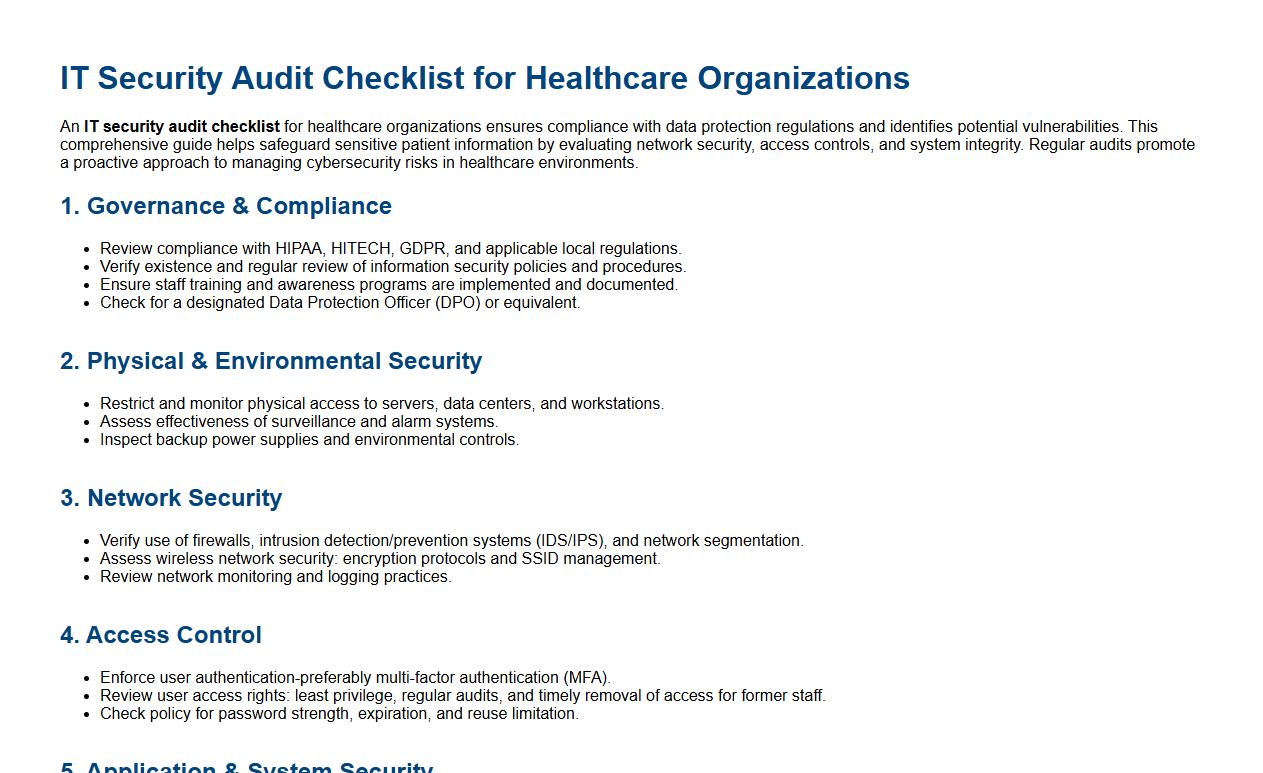
An IT security audit checklist for healthcare organizations ensures compliance with data protection regulations and identifies potential vulnerabilities. This comprehensive guide helps safeguard sensitive patient information by evaluating network security, access controls, and system integrity. Regular audits promote a proactive approach to managing cybersecurity risks in healthcare environments.
IT security audit checklist for remote work environments
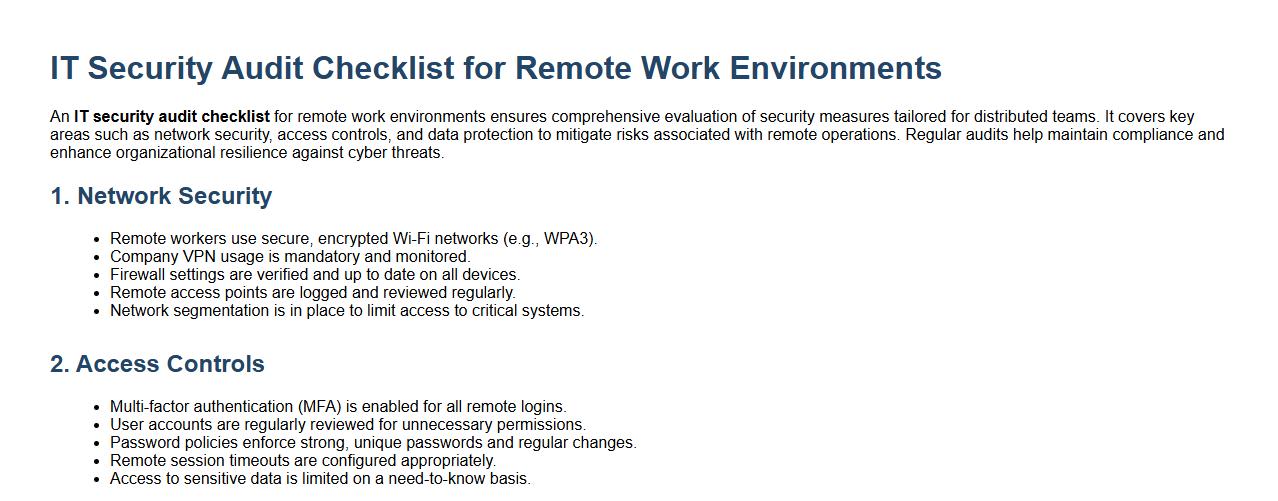
An IT security audit checklist for remote work environments ensures comprehensive evaluation of security measures tailored for distributed teams. It covers key areas such as network security, access controls, and data protection to mitigate risks associated with remote operations. Regular audits help maintain compliance and enhance organizational resilience against cyber threats.
Cloud IT security audit checklist for hybrid infrastructures

A comprehensive Cloud IT security audit checklist ensures hybrid infrastructures maintain robust protection against evolving cyber threats. It covers key areas such as access controls, data encryption, and compliance with industry standards. Regular audits help identify vulnerabilities and strengthen overall cloud security posture.
IT security audit checklist for compliance with GDPR

Ensure your organization adheres to data protection regulations with this comprehensive IT security audit checklist tailored for GDPR compliance. It covers key areas such as access controls, data encryption, and breach response protocols. Regular audits help identify vulnerabilities and maintain robust security standards.
Internal IT security audit checklist for data protection
Conducting an Internal IT security audit is essential for ensuring robust data protection measures are in place. This checklist helps identify vulnerabilities, assess compliance with security policies, and implement corrective actions to safeguard sensitive information. Regular audits strengthen overall cybersecurity and reduce the risk of data breaches.
Cybersecurity IT security audit checklist for SaaS companies
Ensure your SaaS company's safety with a comprehensive Cybersecurity IT security audit checklist designed to identify vulnerabilities and enforce robust protection measures. This checklist covers all critical aspects, from data encryption to access controls, helping maintain compliance and safeguard sensitive information. Regular audits using this guide will strengthen your security posture and build customer trust.
IT security audit checklist for network vulnerability assessment

Conducting an IT security audit checklist for network vulnerability assessment ensures comprehensive identification of potential threats and weaknesses. This process helps organizations safeguard their data by systematically evaluating network components and configurations. Regular audits enhance overall security posture and compliance with industry standards.
IT security audit checklist for PCI DSS compliance

Ensure your organization meets all requirements with our comprehensive IT security audit checklist for PCI DSS compliance. This checklist guides you through critical security controls to protect cardholder data and maintain regulatory standards. Regular audits help identify vulnerabilities and strengthen your overall security posture.
Are all IT security policies referenced in the audit checklist up-to-date and version-controlled?
Ensuring that all IT security policies referenced in the audit checklist are up-to-date is crucial for compliance and risk management. Version control guarantees that the latest policies are in place, preventing outdated practices from being audited. Regular reviews and updates of the checklist maintain its relevance and accuracy.
Does the checklist verify secure disposal processes for hardcopy and digital audit documents?
The audit checklist must include verification of secure disposal processes for both hardcopy and digital documents to prevent data leaks. Proper disposal methods such as shredding and secure deletion are essential to protect sensitive information. Compliance with data protection regulations hinges on thorough disposal verification.
Is there a section on evidence collection procedures for privilege escalation activities?
An effective checklist incorporates specific procedures for evidence collection related to privilege escalation activities to identify malicious behavior. This ensures audit trails are complete and admissible for forensic analysis. Accurate documentation aids in timely investigation and mitigation of security breaches.
Does the checklist address encryption methods for storing and transmitting sensitive audit letters?
The checklist should mandate the use of encryption methods for secure storage and transmission of sensitive audit letters. Encryption protects the integrity and confidentiality of audit communications against unauthorized access. Implementing strong encryption protocols is a core component of IT security audits.
Are digital signatures required and validated for all IT security audit correspondence?
Requiring and validating digital signatures ensures authenticity and non-repudiation in all IT security audit correspondence. This practice enhances trust and accountability between auditors and stakeholders. Digitally signed documents also comply with legal and regulatory standards.
