
A Security Log Form Sample is a structured document used to record security-related incidents, access details, and unusual activities within a facility. This form helps maintain accurate and organized records for monitoring and investigating security breaches. It typically includes fields for date, time, description of the event, and personnel involved.
Downloadable security log form sample PDF
Download our security log form sample in PDF format to efficiently record and monitor security activities. This template is designed for easy customization and comprehensive tracking of incidents and observations. Utilize the form to enhance your security documentation and maintain detailed logs.
Daily security activity log form sample
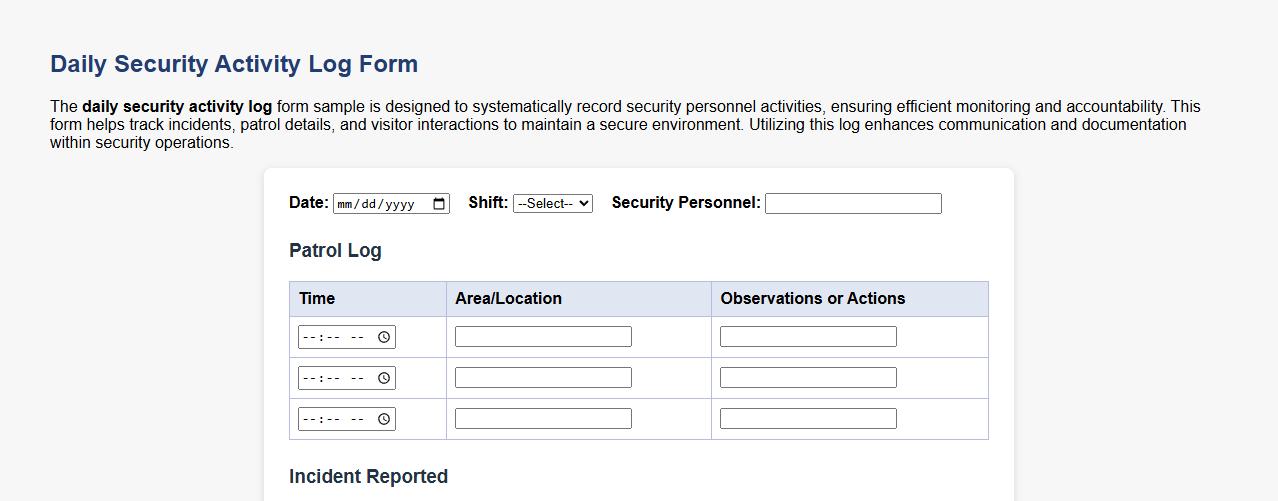
The daily security activity log form sample is designed to systematically record security personnel activities, ensuring efficient monitoring and accountability. This form helps track incidents, patrol details, and visitor interactions to maintain a secure environment. Utilizing this log enhances communication and documentation within security operations.
Security guard incident log form sample
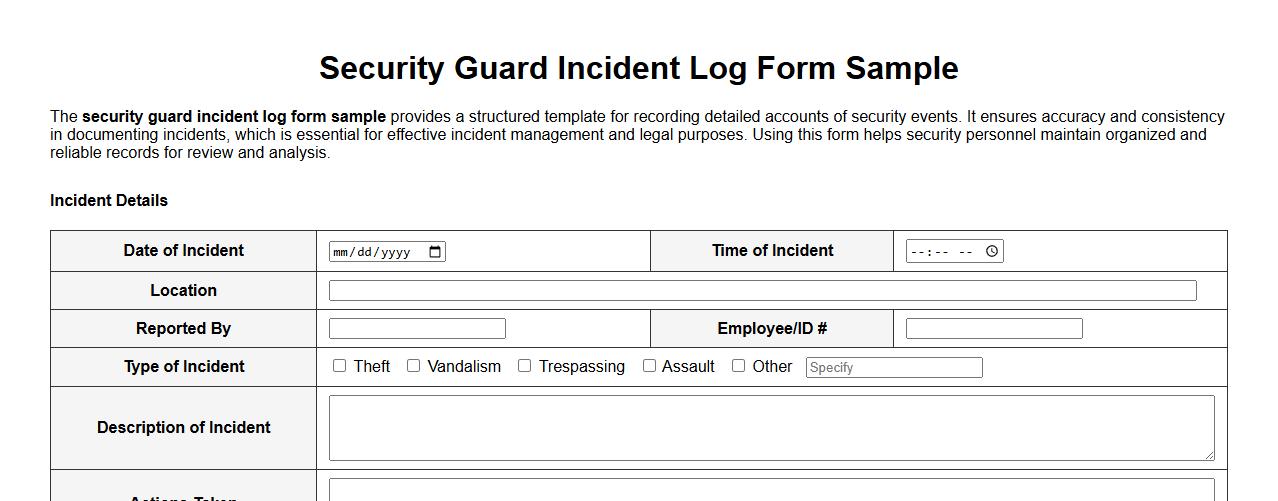
The security guard incident log form sample provides a structured template for recording detailed accounts of security events. It ensures accuracy and consistency in documenting incidents, which is essential for effective incident management and legal purposes. Using this form helps security personnel maintain organized and reliable records for review and analysis.
Building security log form sample template
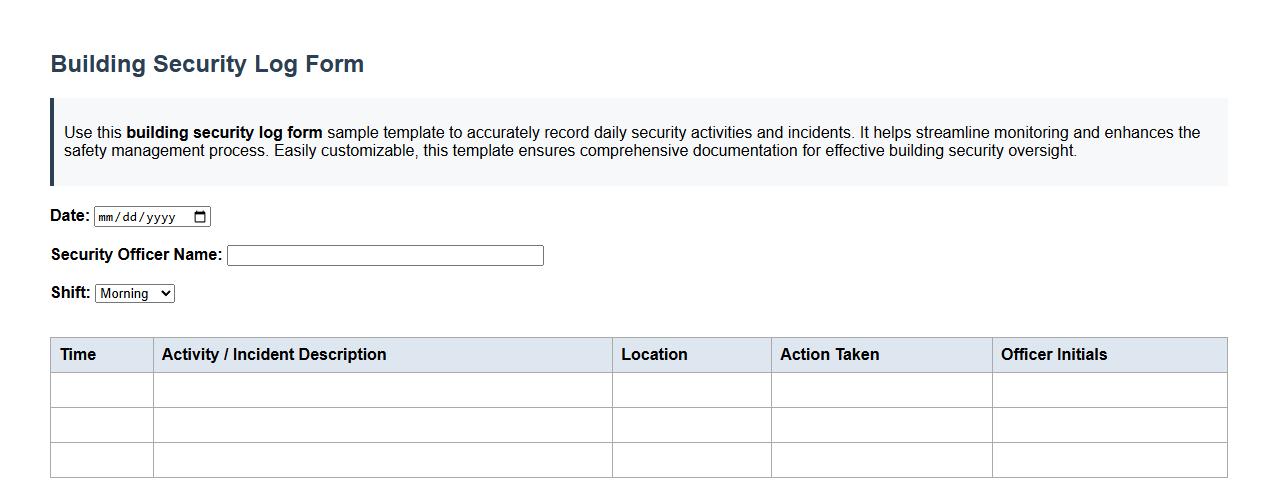
Use this building security log form sample template to accurately record daily security activities and incidents. It helps streamline monitoring and enhances the safety management process. Easily customizable, this template ensures comprehensive documentation for effective building security oversight.
Security patrol log form sample for hotels
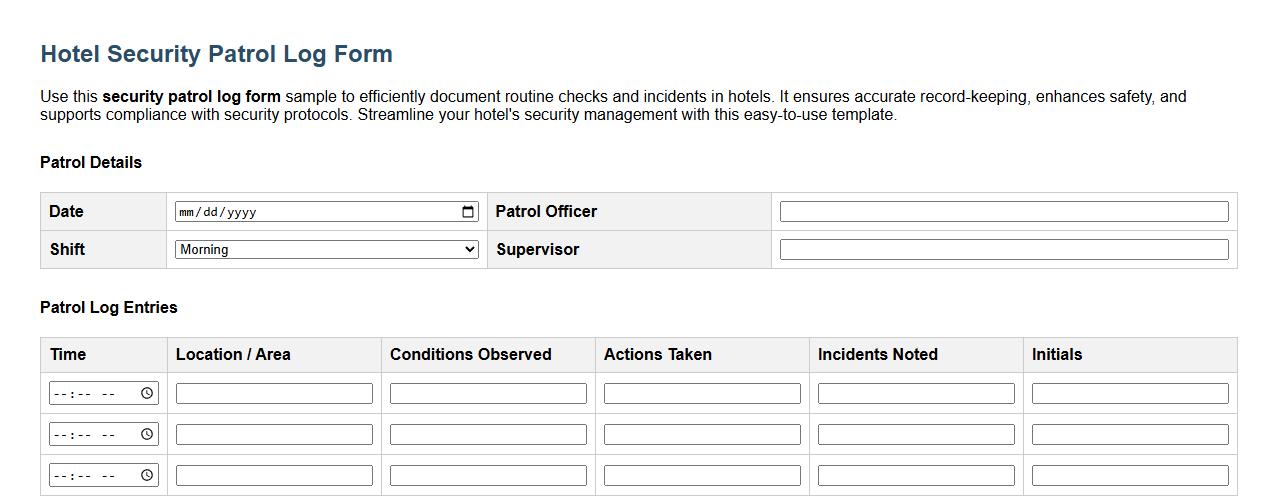
Use this security patrol log form sample to efficiently document routine checks and incidents in hotels. It ensures accurate record-keeping, enhances safety, and supports compliance with security protocols. Streamline your hotel's security management with this easy-to-use template.
Detailed security checkpoint log form sample
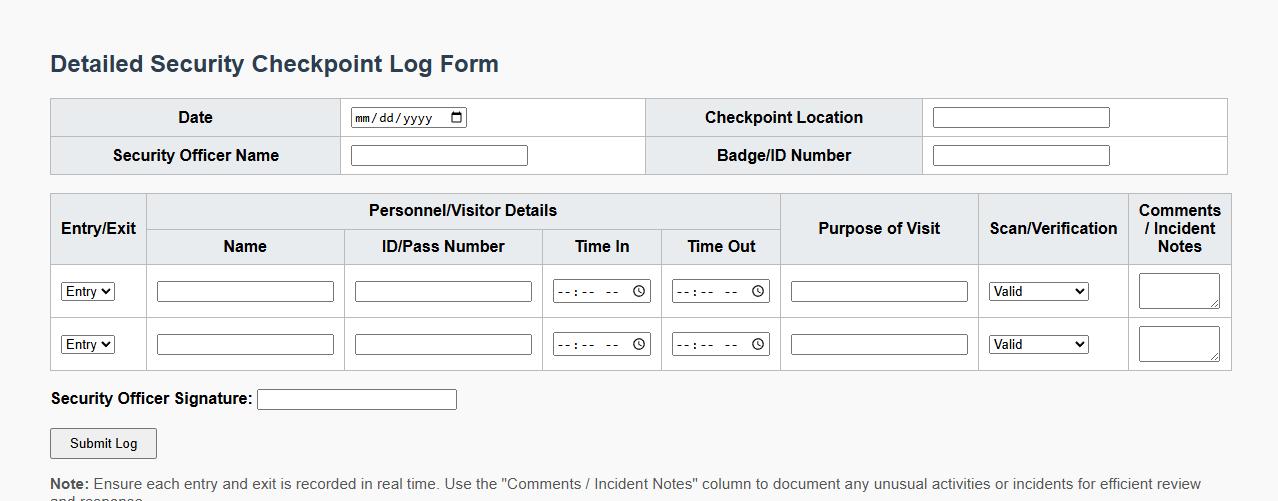
This detailed security checkpoint log form sample is designed to accurately record all entries and exits, ensuring comprehensive monitoring. It includes fields for date, time, personnel details, and incident notes to maintain a robust security audit trail. Utilizing this form enhances accountability and aids in quick incident response.
Security visitor log form sample for businesses
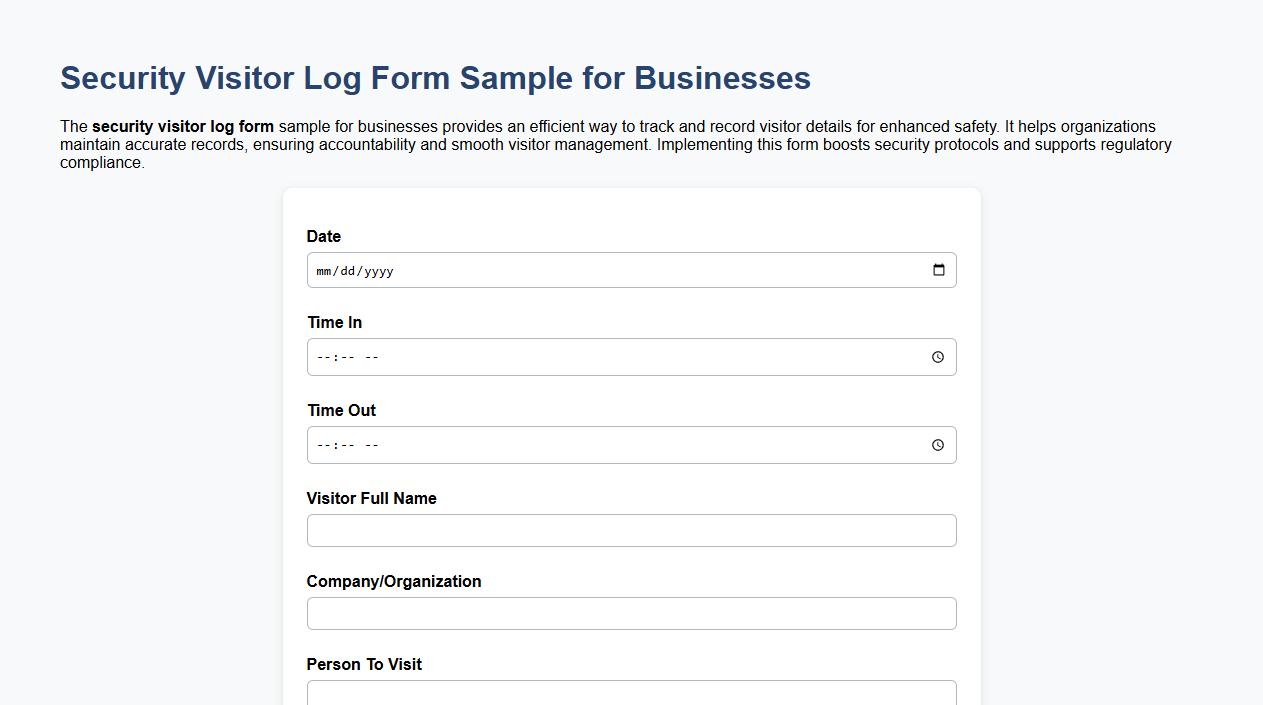
The security visitor log form sample for businesses provides an efficient way to track and record visitor details for enhanced safety. It helps organizations maintain accurate records, ensuring accountability and smooth visitor management. Implementing this form boosts security protocols and supports regulatory compliance.
Construction site security log form sample
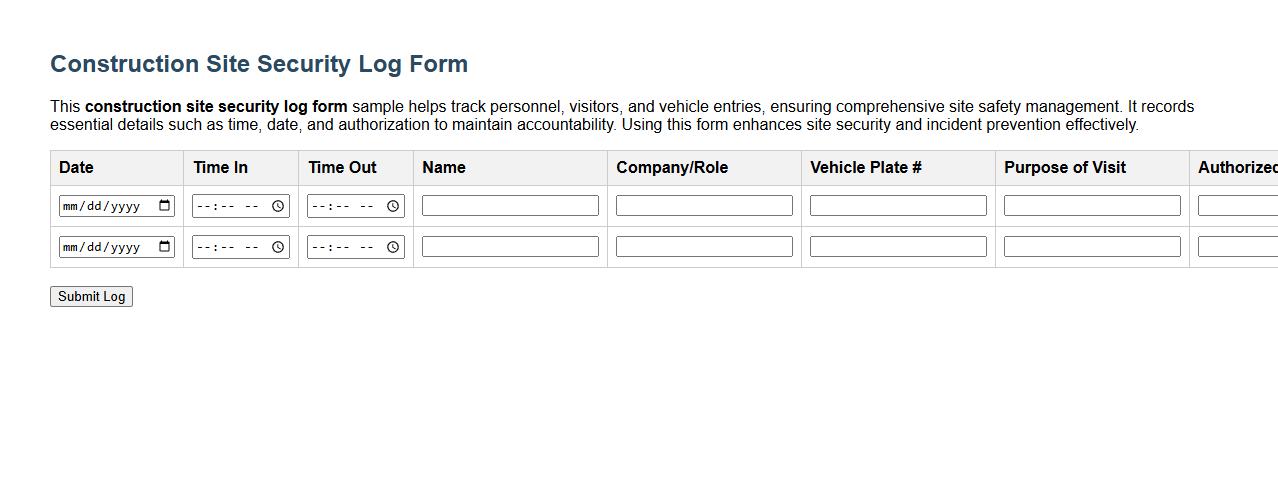
This construction site security log form sample helps track personnel, visitors, and vehicle entries, ensuring comprehensive site safety management. It records essential details such as time, date, and authorization to maintain accountability. Using this form enhances site security and incident prevention effectively.
Security shift handover log form sample
The security shift handover log form sample is a crucial document used to ensure seamless communication between outgoing and incoming security personnel. It helps in recording important information, incidents, and instructions to maintain security continuity. This form enhances accountability and operational efficiency during shift changes.
What fields are essential for tracking entry and exit times in a Security Log Form?
The entry time and exit time fields are crucial for accurately recording when individuals access and leave a facility. Additional fields such as the visitor's name, purpose of visit, and ID verification help in maintaining comprehensive logs. These details ensure reliable monitoring of access patterns and enhance security measures.
How can digital Security Log Forms enhance document traceability?
Digital Security Log Forms improve document traceability by automatically timestamping entries and maintaining a detailed audit trail. They enable real-time access and updates, which reduces the risk of tampering and data loss. Furthermore, digital logs simplify searching and reporting, providing efficient management of security records.
Which authentication methods are recommended for signing Security Log Forms?
Multi-factor authentication (MFA) is recommended for signing Security Log Forms, combining passwords with biometric verification or one-time codes. Digital signatures ensure the integrity and authenticity of the logged data. These methods prevent unauthorized access and enhance overall security compliance.
What data retention policies apply to Security Log Forms in regulated industries?
Regulated industries often require Security Log Forms to be retained for a specified period, typically between 3 to 7 years, depending on jurisdiction. Policies mandate secure storage and controlled access to meet compliance standards. Proper retention ensures legal readiness and supports audits and investigations.
How do you ensure confidentiality when archiving Security Log Forms?
Confidentiality is maintained by encrypting Security Log Forms during both storage and transmission. Access controls and role-based permissions limit availability to authorized personnel only. Regular audits and secure backup systems further protect sensitive security data from unauthorized disclosure.
