
A Access Request Form Sample serves as a template to streamline the process of requesting access to secure systems, data, or facilities. This standard form includes essential fields such as requester details, access level required, and justification for access, ensuring clarity and compliance. Utilizing a well-designed Access Request Form Sample enhances security by systematically documenting and approving access permissions.
Employee access request form sample
Use this employee access request form sample to streamline the process of granting access permissions within your organization. The form ensures that access rights are documented, authorized, and tracked efficiently. It helps maintain security and compliance by clearly defining user roles and access levels.
Data center access request form sample
This data center access request form sample streamlines the process of granting authorized personnel entry to secure data center facilities. It includes fields for applicant information, access level, and reason for entry, ensuring compliance with security protocols. Utilizing this form enhances confidentiality and operational efficiency within IT environments.
System access request form sample
The system access request form sample is designed to streamline the process of granting user permissions securely. It ensures that all necessary information is collected to evaluate and approve access efficiently. Utilizing this form helps maintain system integrity and compliance with security policies.
Building access request form sample
Use this building access request form sample to streamline the process of granting authorized entry to your premises. It ensures all necessary information is collected for security and record-keeping purposes. Simplify access management with a clear and efficient request template.
Physical access request form sample
This physical access request form sample streamlines the process of granting authorized personnel entry to secure areas. Designed for clarity and compliance, it ensures all necessary information is collected efficiently. Utilizing this form helps maintain security protocols while facilitating smooth access management.
Temporary access request form sample
This temporary access request form sample streamlines the process of granting short-term entry permissions, ensuring security and accountability. It captures essential details such as user information, access duration, and approval signatures. Utilizing this form helps organizations maintain control over temporary access while complying with internal policies.
Network access request form sample
This network access request form sample is designed to streamline the process of granting user permissions to secure network resources. It ensures all necessary information is collected for proper evaluation and authorization. Using this template helps maintain network security and compliance efficiently.
Visitor access request form sample
This visitor access request form sample helps organizations manage and authorize entry to secure areas efficiently. It streamlines the process by collecting essential visitor information and approval details. Using this form ensures enhanced security and smooth visitor management.
Remote access request form sample
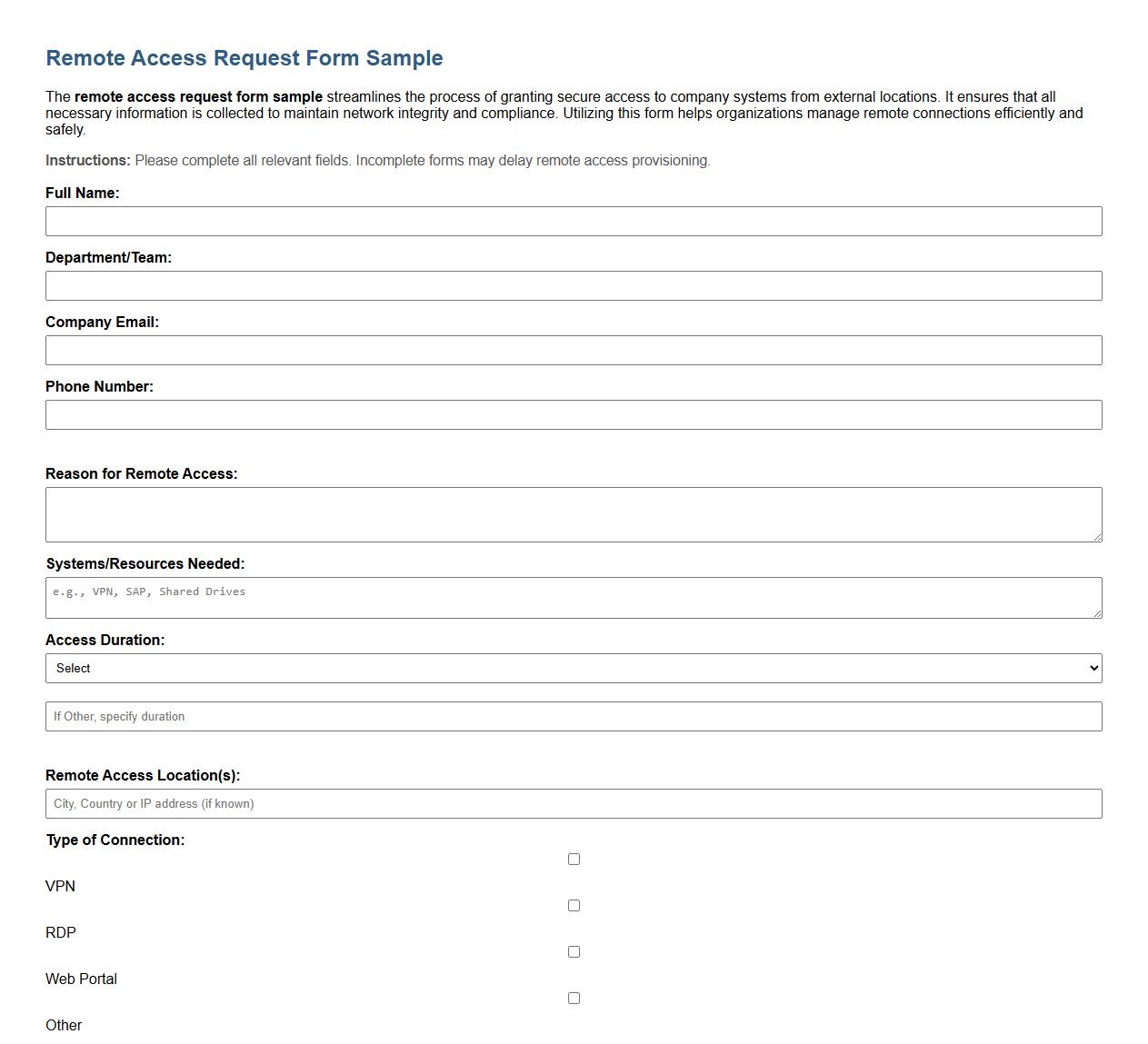
The remote access request form sample streamlines the process of granting secure access to company systems from external locations. It ensures that all necessary information is collected to maintain network integrity and compliance. Utilizing this form helps organizations manage remote connections efficiently and safely.
User account access request form sample
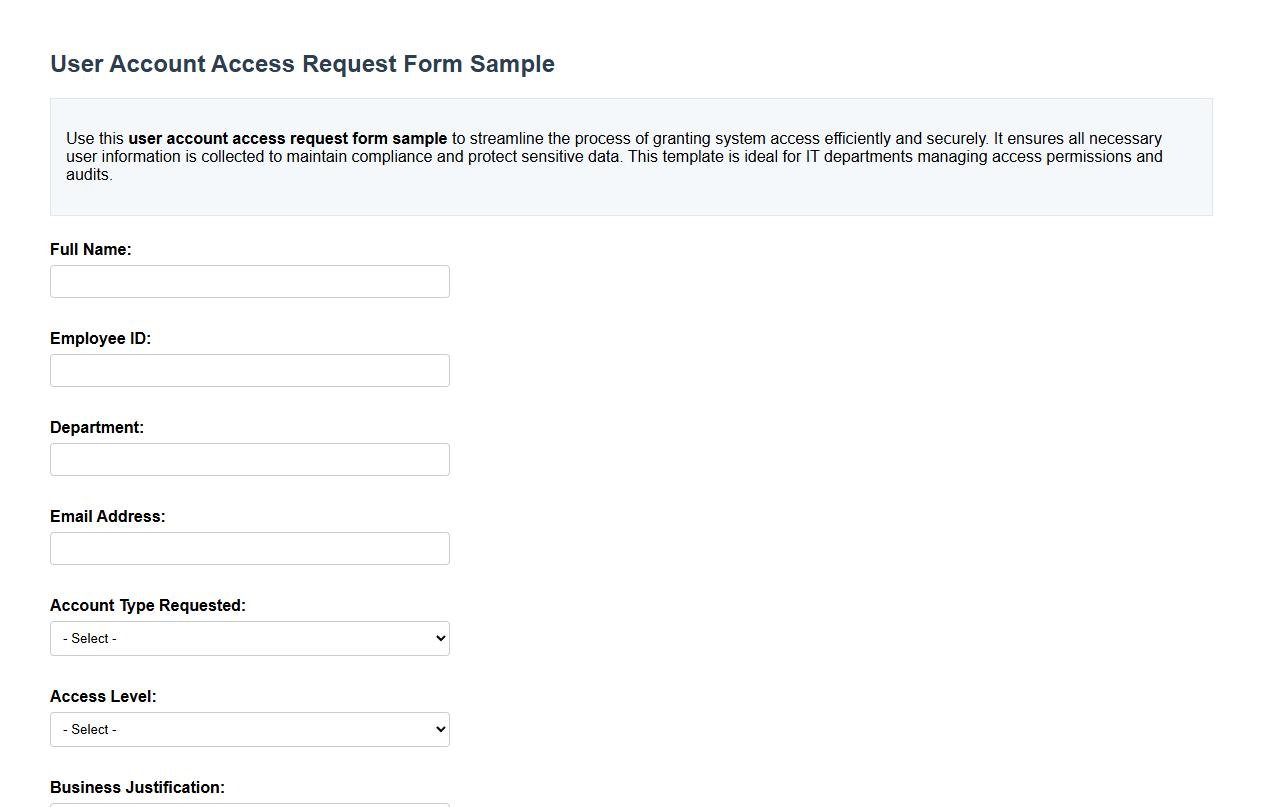
Use this user account access request form sample to streamline the process of granting system access efficiently and securely. It ensures all necessary user information is collected to maintain compliance and protect sensitive data. This template is ideal for IT departments managing access permissions and audits.
Which specific data fields are mandatory on the Access Request Form for compliance?
The mandatory data fields on the Access Request Form typically include the requestor's full name, department, and contact information. Additionally, the form requires detailed information about the requested access level and system or resource. These fields ensure compliance with organizational and regulatory policies for access management.
How is user role justification documented within the Access Request Form?
User role justification is documented by providing a clear and concise explanation of the business need for the requested access. The form includes a dedicated section where the requestor must describe their duties and how the access supports their role. This documentation is critical for validating the necessity and appropriateness of the access level.
What process is followed for multi-level approval signatures on the Access Request Form?
The Access Request Form requires sequential multi-level approvals starting from the direct supervisor, followed by the department head and IT security. Each approver must sign and date the form to confirm their review and authorization. This process ensures a thorough audit trail and enforces accountability throughout the approval chain.
Are there version controls or audit trails embedded within the Access Request Form template?
The Access Request Form template incorporates version control to track changes and maintain consistency across submissions. An embedded audit trail records each modification, approval, and submission date for compliance and review purposes. These features enhance transparency and support regulatory compliance efforts.
How is sensitive information protected during the submission of the Access Request Form?
Sensitive information on the Access Request Form is protected through encryption during electronic transmission and secure storage protocols. Access to the submitted forms is restricted to authorized personnel only, enforced by strict role-based access controls. These measures ensure the confidentiality and integrity of sensitive data throughout the submission process.
