
A Vulnerability Assessment Form Sample is a structured template used to systematically identify and document potential security weaknesses within an organization's systems. It helps prioritize risks by detailing vulnerabilities, their severity, and recommended mitigation strategies. This form is essential for maintaining proactive security measures and ensuring compliance with industry standards.
Vulnerability assessment form sample for small business
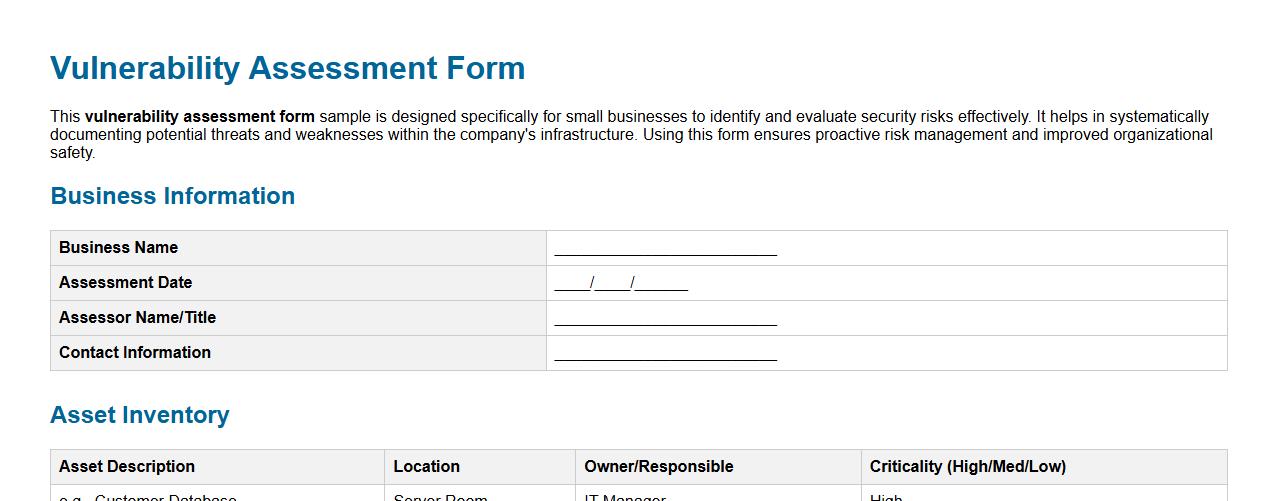
This vulnerability assessment form sample is designed specifically for small businesses to identify and evaluate security risks effectively. It helps in systematically documenting potential threats and weaknesses within the company's infrastructure. Using this form ensures proactive risk management and improved organizational safety.
Cybersecurity vulnerability assessment form sample
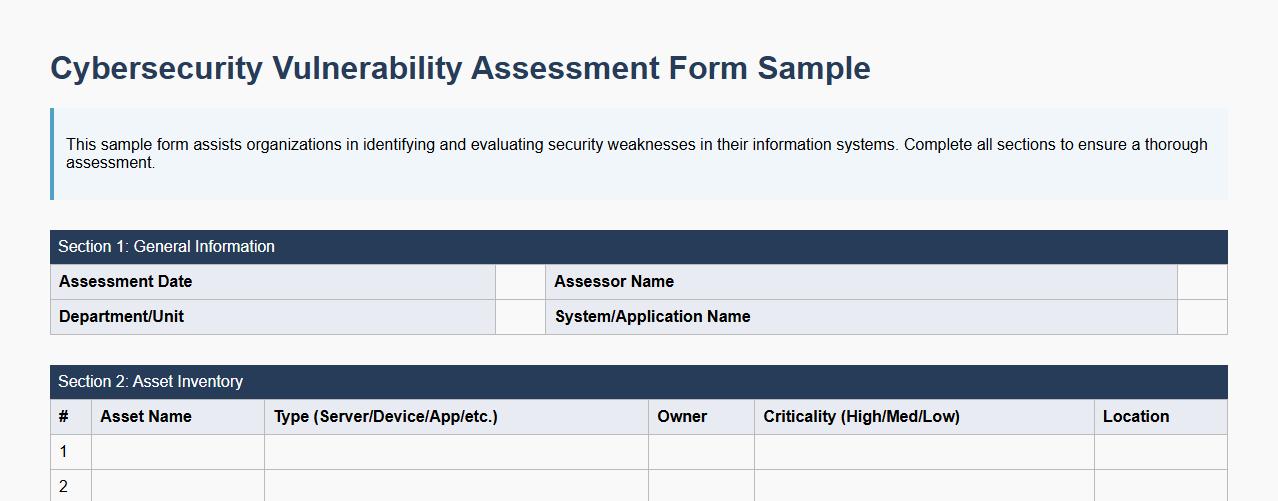
A cybersecurity vulnerability assessment form sample helps organizations systematically identify and evaluate security weaknesses in their systems. This form typically includes sections for asset inventory, threat analysis, and risk prioritization to enhance protection strategies. Using a standardized form ensures consistent and thorough vulnerability assessments across all departments.
Physical security vulnerability assessment form sample
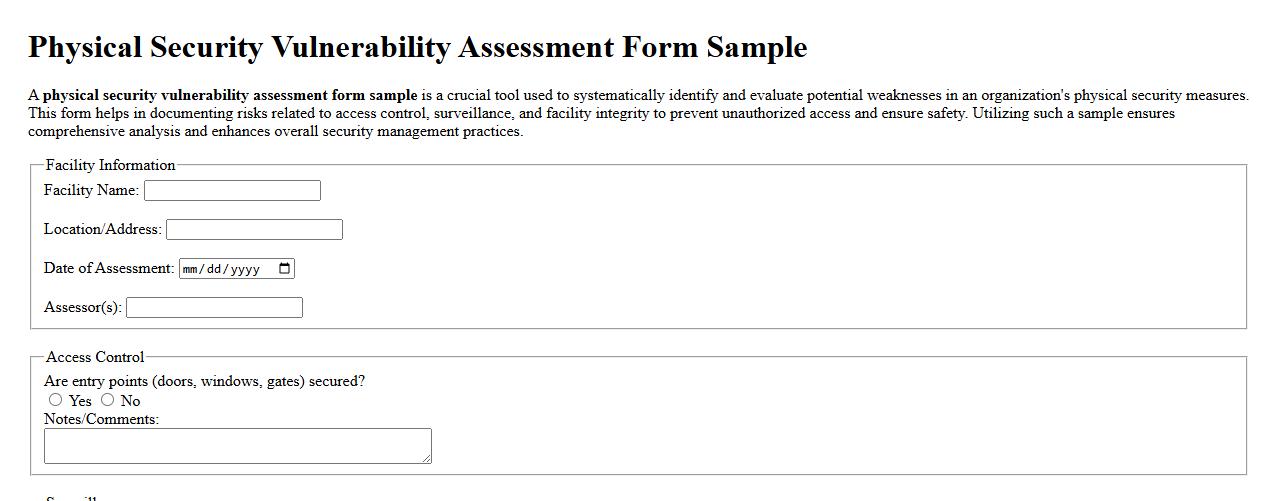
A physical security vulnerability assessment form sample is a crucial tool used to systematically identify and evaluate potential weaknesses in an organization's physical security measures. This form helps in documenting risks related to access control, surveillance, and facility integrity to prevent unauthorized access and ensure safety. Utilizing such a sample ensures comprehensive analysis and enhances overall security management practices.
IT network vulnerability assessment form sample
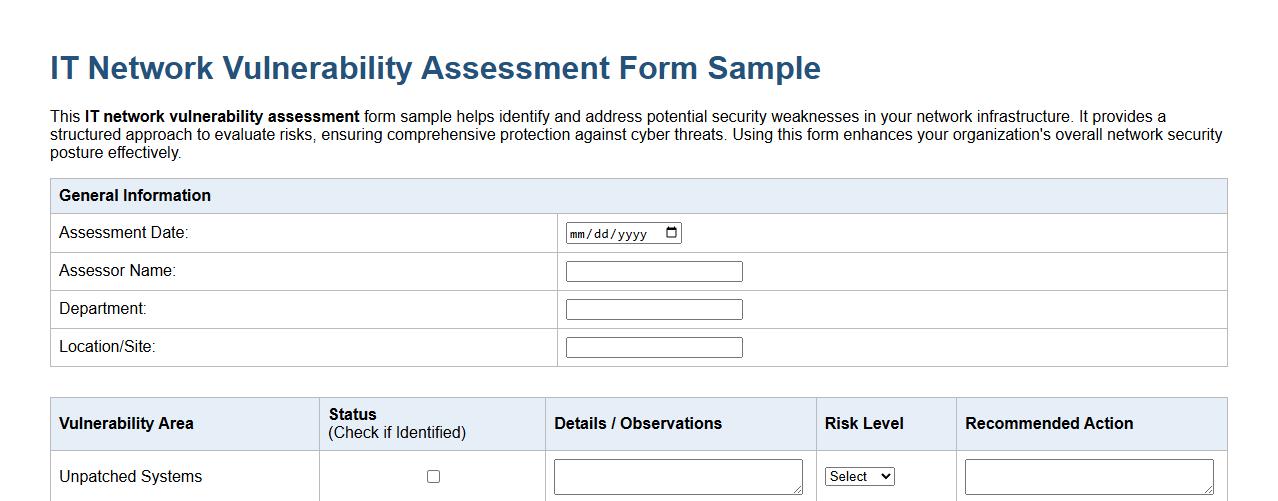
This IT network vulnerability assessment form sample helps identify and address potential security weaknesses in your network infrastructure. It provides a structured approach to evaluate risks, ensuring comprehensive protection against cyber threats. Using this form enhances your organization's overall network security posture effectively.
Environmental vulnerability assessment form sample
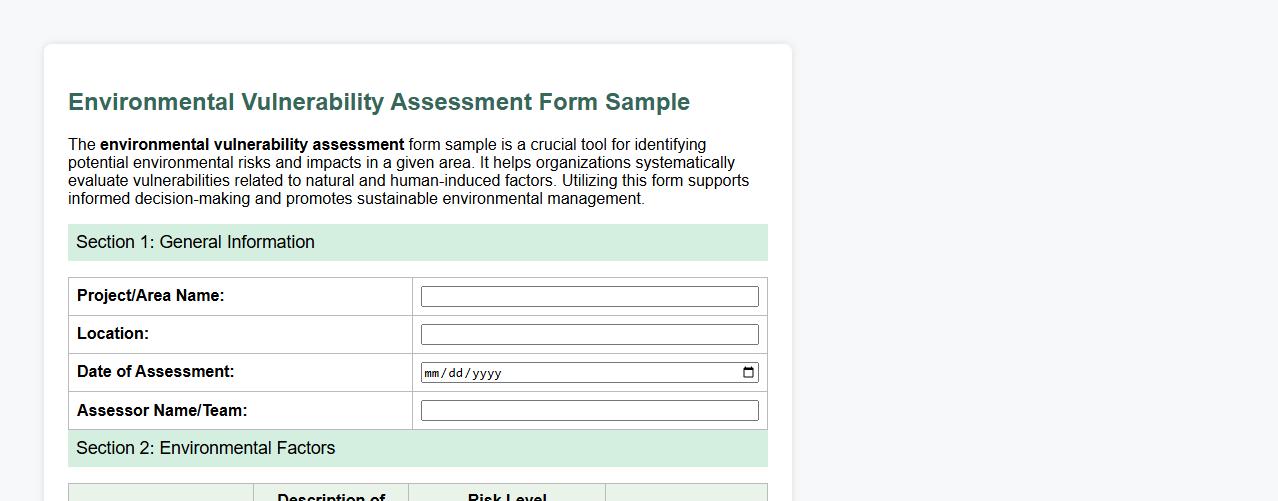
The environmental vulnerability assessment form sample is a crucial tool for identifying potential environmental risks and impacts in a given area. It helps organizations systematically evaluate vulnerabilities related to natural and human-induced factors. Utilizing this form supports informed decision-making and promotes sustainable environmental management.
Vulnerability assessment form sample for schools
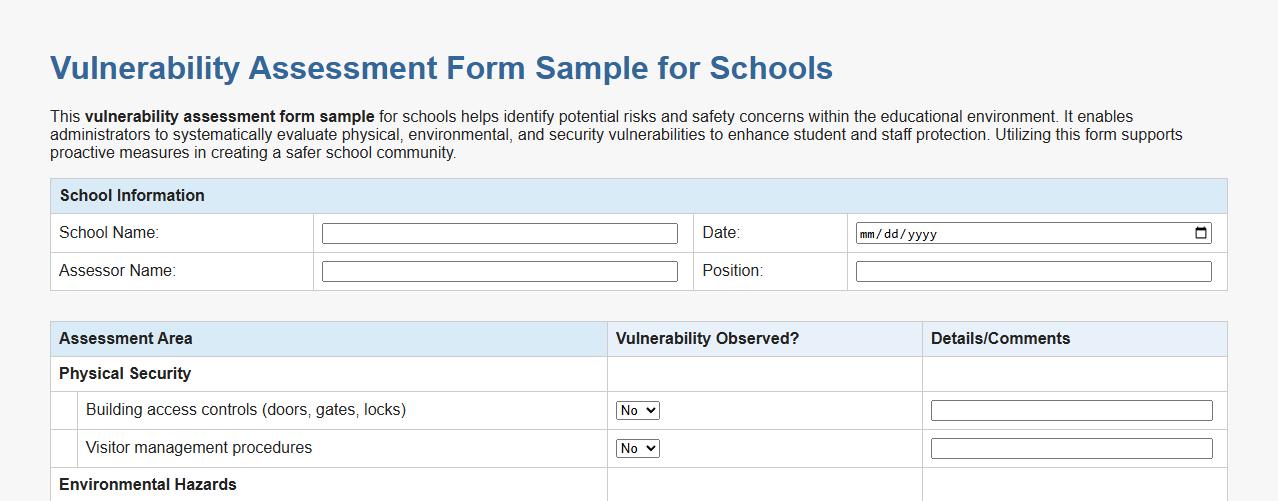
This vulnerability assessment form sample for schools helps identify potential risks and safety concerns within the educational environment. It enables administrators to systematically evaluate physical, environmental, and security vulnerabilities to enhance student and staff protection. Utilizing this form supports proactive measures in creating a safer school community.
Risk and vulnerability assessment form sample
A risk and vulnerability assessment form sample is a structured template designed to identify and evaluate potential hazards and weaknesses in a system or organization. It helps prioritize risks by assessing their impact and likelihood, enabling informed decision-making for mitigation strategies. Utilizing this form ensures a comprehensive approach to enhancing security and resilience.
Data center vulnerability assessment form sample
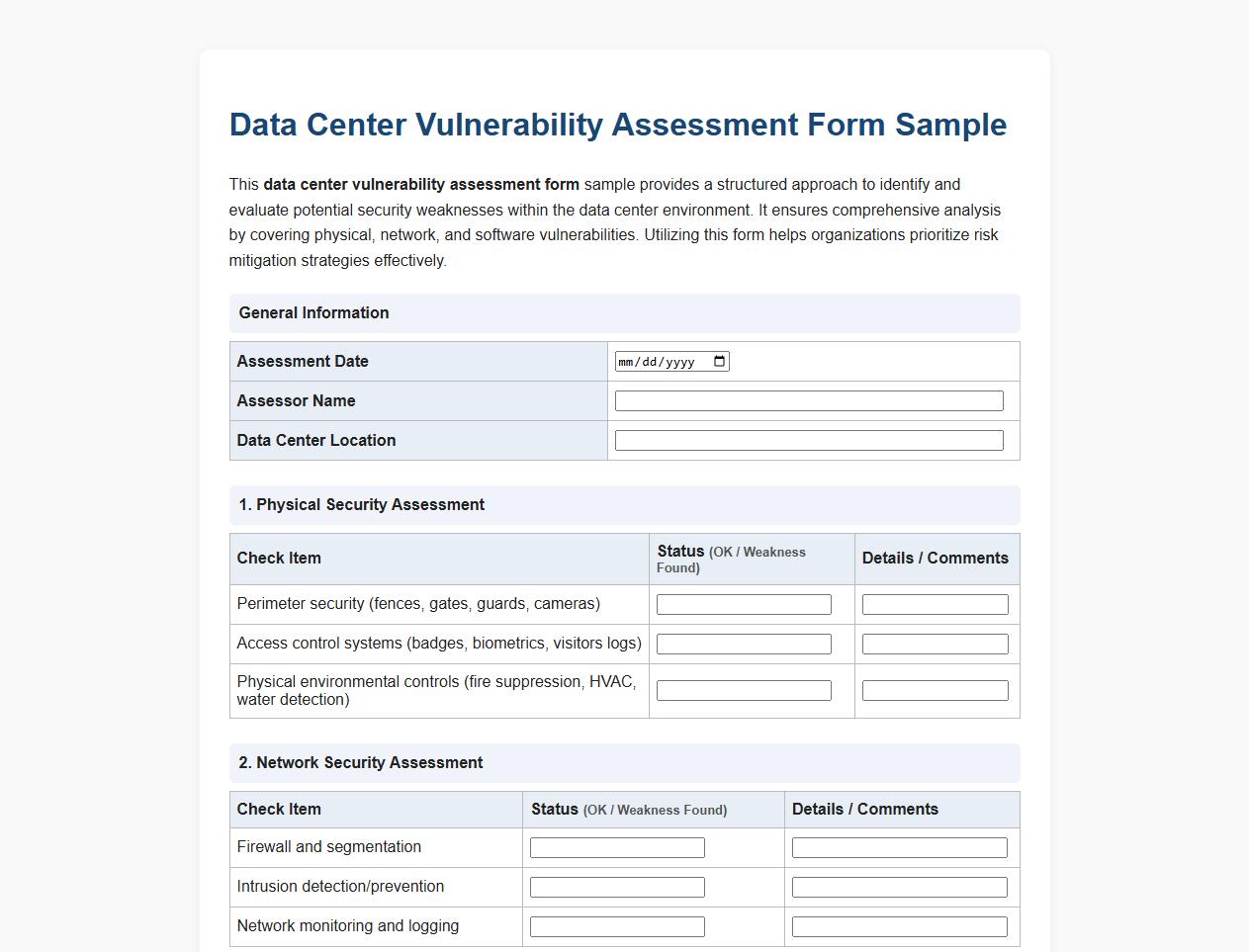
This data center vulnerability assessment form sample provides a structured approach to identify and evaluate potential security weaknesses within the data center environment. It ensures comprehensive analysis by covering physical, network, and software vulnerabilities. Utilizing this form helps organizations prioritize risk mitigation strategies effectively.
Building vulnerability assessment form sample
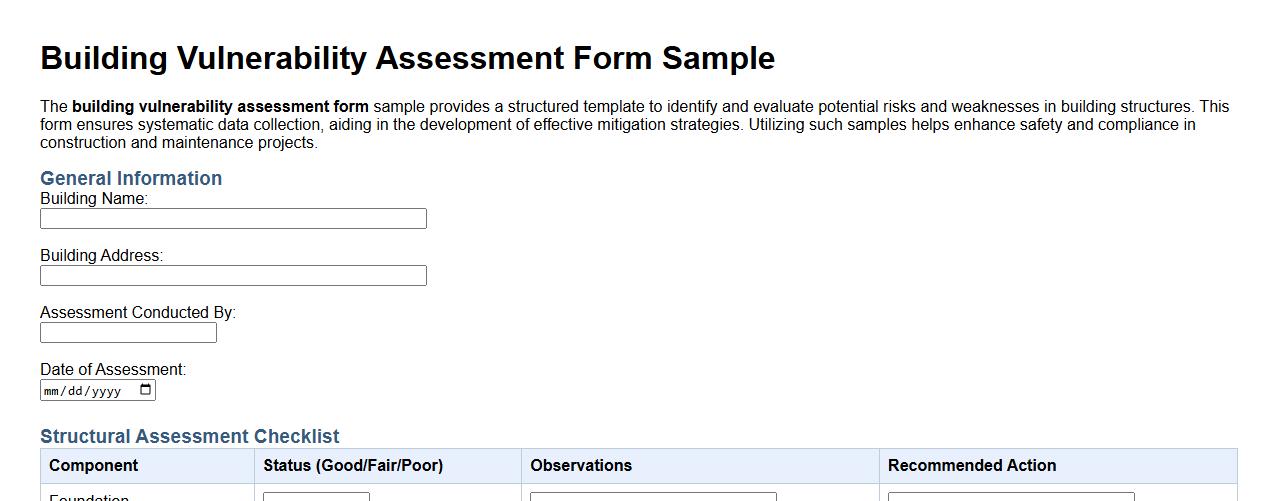
The building vulnerability assessment form sample provides a structured template to identify and evaluate potential risks and weaknesses in building structures. This form ensures systematic data collection, aiding in the development of effective mitigation strategies. Utilizing such samples helps enhance safety and compliance in construction and maintenance projects.
Healthcare vulnerability assessment form sample
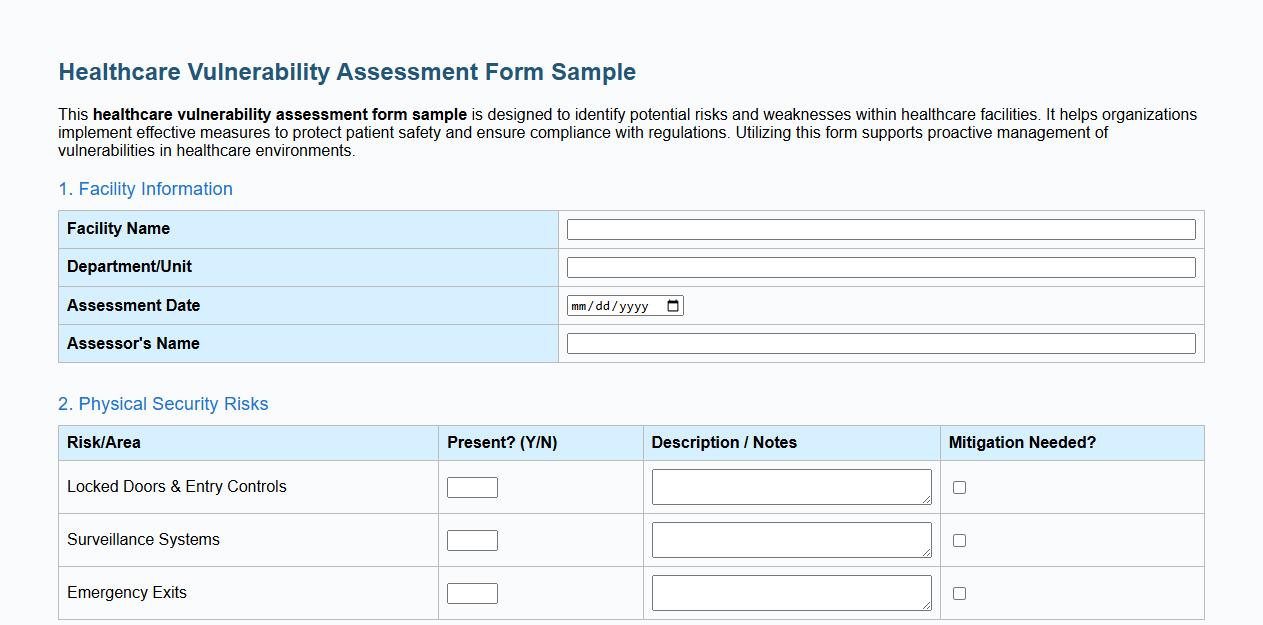
This healthcare vulnerability assessment form sample is designed to identify potential risks and weaknesses within healthcare facilities. It helps organizations implement effective measures to protect patient safety and ensure compliance with regulations. Utilizing this form supports proactive management of vulnerabilities in healthcare environments.
What critical vulnerabilities are prioritized in this Vulnerability Assessment Form?
The form prioritizes critical vulnerabilities such as remote code execution, privilege escalation, and data exposure flaws. It emphasizes weaknesses that pose immediate threats to system integrity and confidentiality. Identifying these vulnerabilities helps focus remediation efforts on high-risk areas.
How does the form categorize risk severity for discovered vulnerabilities?
The form categorizes risk severity into low, medium, high, and critical levels based on impact and exploitability. Each vulnerability is assessed for its potential damage and likelihood of exploitation. This structured approach aids in prioritizing vulnerabilities for remediation.
Which compliance frameworks are referenced within the form's assessment criteria?
The assessment criteria reference major compliance frameworks such as PCI-DSS, HIPAA, and NIST. These frameworks guide the evaluation of vulnerabilities against industry standards and regulatory requirements. Including such frameworks ensures comprehensive risk management and compliance.
Is there a section for documenting exploitable vectors and potential impact scenarios?
The form includes a dedicated section to document exploitable vectors and potential impact scenarios. This section helps in understanding how vulnerabilities may be leveraged and the consequences of exploitation. Detailed documentation supports informed decision-making in vulnerability management.
Does the form require evidence or documentation for remediation actions taken?
Yes, the form requires evidence and documentation of all remediation actions to verify vulnerabilities have been addressed. This includes patching records, configuration changes, and validation tests. Providing evidence ensures accountability and helps track the effectiveness of fixes.
